This article is a guide on how to protect your online privacy. It emphasises on using a VPN as one of the ways to protect your privacy online.
Your online privacy has been compromised.
Yes, you read it right.
You think using the internet from our personal device keeps us secure. You think there is no one between your device and the website you are accessing.
So You text, You email, You follow, You tweet, You like, You comment, You tag, and You use hashtag because no one is watching you. But everything you do on the internet is monitored.
Incognito mode is not the way out! Using the incognito mode will not create logs and history on your computer, but it doesn’t mean you have not been watched.
So how does it all happen?
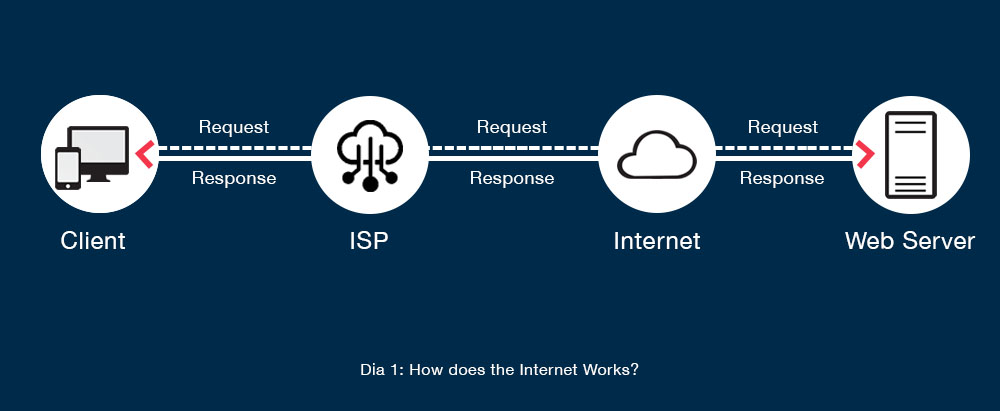
Internet connection, be it cable or wireless, comes from an ISP (Internet Service Provider). ISP connects you to websites you visit and the data you access from the web servers. On the internet, data transmission is done through data packets, which are fixed in size. Each packet has the sender and receiver’s IP addresses.
Let’s say you want to access a webpage. You type the URL of that website in the address bar of your browser, or you search it via a search engine. Your computer sends a data packet to your ISP requesting the webpage.
Your ISP again sends data packets over the internet to the particular web server. Now the web server sends data packets to your ISP, and then you receive those packets to your computer to decode them as a web page.
Complicated?
Yes, it is! Take a look at this image. That’s how the internet works.
I See You!!!
In this process, your ISP can see what domains you are accessing. If you are visiting a non-SSL site, then your data transmission is not encrypted. This means everything you do on that website is not secure. Even if the website you are accessing is SSL secured website which is encrypted, ISP can track your activities.
For example, by monitoring the individual packet’s size, pattern and timing, your ISP can guess receiver of a message or the length of your password. Obviously, your ISP guys are not seated with popcorns and watching over your personal data, but that doesn’t mean it’s not a concern.
All these logs are stored automatically. So, your ISP knows it all, and they can use your personal data.
It’s just not the malicious people who hack your data.
Government agencies run surveillance programs to keep track of activities happening on the internet. A very famous whistleblower leaked data about how the government tracks your personal data (be it on SSL sites) and your private movements over the internet. WikiLeaks recently published a report on hacking tools used by CIA. These surveillance programs contain logs of your metadata (data about data; here you are a digital data) spying on your online privacy.
Sometimes Data Stealing is gift wrapped in an attractive package.
Major websites offer their services for free, like Google and Facebook. A saying says, if you are not paying for the product, then you are the product. We use such services for free. Actually, that is a myth. We trade our personal information for such services. Web giants have data warehouses to store this big data. Everything you search on the internet, every video you watch online, every post you share on the social media is stored and analyzed.
Wait, do they see the memes I like? 😐
So what is actually secured?
Nothing!
That is the truth.
The messages you send over your favorite messaging app, everything you buy online, where do you go, how do you travel, your daily lifestyle, your heartbeat records from your smartwatches – everything is actually tracked and stored.
Giant data warehouses maintain the digital version of you and your metadata. Every time you visit a website again, they give you results from your past usage of their services. The technique used is machine learning, and it knows many things about you including how likely you are about to die from heart disease.
Artificial Intelligence and Machine Learning help them to predict your traits and behavior.
Why is your data so valuable?
Your digital profile is worth its value in gold. This data is often sold to advertisers for interaction with you. Your metadata is categorized in a particular personality group.
For example: On Facebook, if you have liked some soccer pages and you like to view posts from them, then you are categorized into a group named Soccer/US soccer fans ( high content engagement ).
Go to your facebook settings -> Account Settings -> Ads -> Your Information -> Your categories ( Review and Manage Your Categories ) for the proof.
And there is no way you can delete this data. Even if you want to delete your social media profile your metadata will remain intact.
No need to mention the recent data breach! -_-
You are tracked even when think you have nothing to give away.
When you post a photo online via your mobile phone, you gift the social media site your location and your mobile phone information. Not tagging your location in a post doesn’t mean nobody will know where you are.
Photos you take every day contain metadata, and computer programs like ExifTool are enough to read information from your images.
Should I stop using social media sites?
Social media makes your private life public. You don’t have to quit social media; there are some good reasons we like to use it. You just have to be okay with the facts that you are the data and social privacy is a myth.
Oh! Should I stop using the Internet?
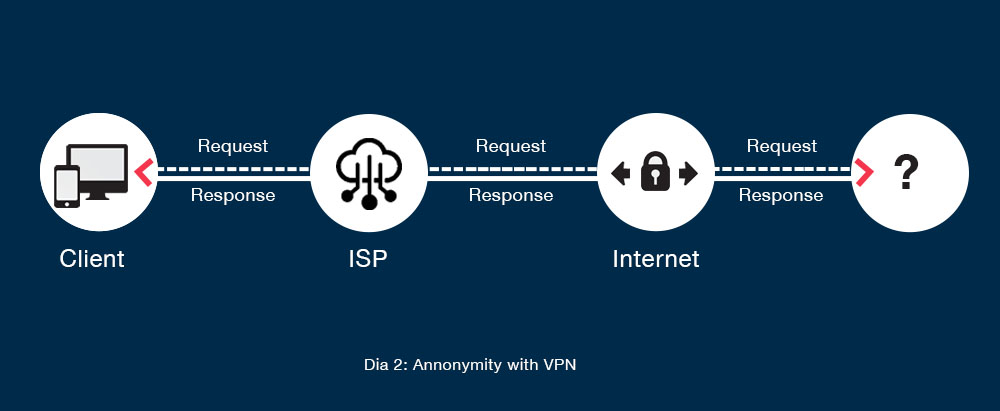
You can’t just stop using the internet. The Internet is an essential part of our life now. But you can find a solution to become anonymous on the internet. VPN is an answer.
VPN stands for Virtual Private Network which uses an encrypted tunnel for transmitting data.
How will VPN help me out?
Your data packets are first sent to the VPN server then to the web server. The VPN server encrypts the data packets. This makes it very difficult for intruders to track your location and decode your data packets.
A VPN server changes your IP address so when someone wants to track your IP address they get VPN server’s IP address. Many VPN service providers have a no logs policy that means they don’t store what sites you visit.
It’s very important to use a good quality VPN service provider if you want to become anonymous over the Internet.
What else for Online Privacy?
TOR ( The Onion Routing ) is another way to enable encrypted communication. TOR creates multiple layers of encryption to hide your data packets over the internet. TOR networking uses multiple nodes ( web servers ) to decode the packets. Each node can decode limited amount of data in a packet though.
Is TOR 100% Safe?
Exit nodes on TOR can leak your location. So it is very important to take precautions while using the TOR network. TOR network is by default a slow network so that data transmission will be slow.
Also, using torrent over TOR is not secure as torrent transmits your IP address while sending data packets. TOR also opens the door of the dark web which we are not covering in this blog post.
A combination of TOR and VPN can be used if you trust your VPN service provider.
Technology today is advancing day by day. This knowledge is limited by the time it is written. You need to be aware of new emerging technologies.
Also, using the internet for legitimate reasons is very important. Using the internet for shady purposes can be harmful to you and others too.